Scans
Instructions
We know now that the attacker uploaded a file called info.php to gain access to the web server backend. What is the name of the tool/shell that gave the attacker a web shell?
Submit the flag as flag{tool_name}. For example: flag{psexec}.
Use the file from Scans.
Solution
Searching for the string info.php leads us to this TCP stream where we see the attacker obtain a shell as the web server user. b374k shell: connected is displayed at the beginning of this session.
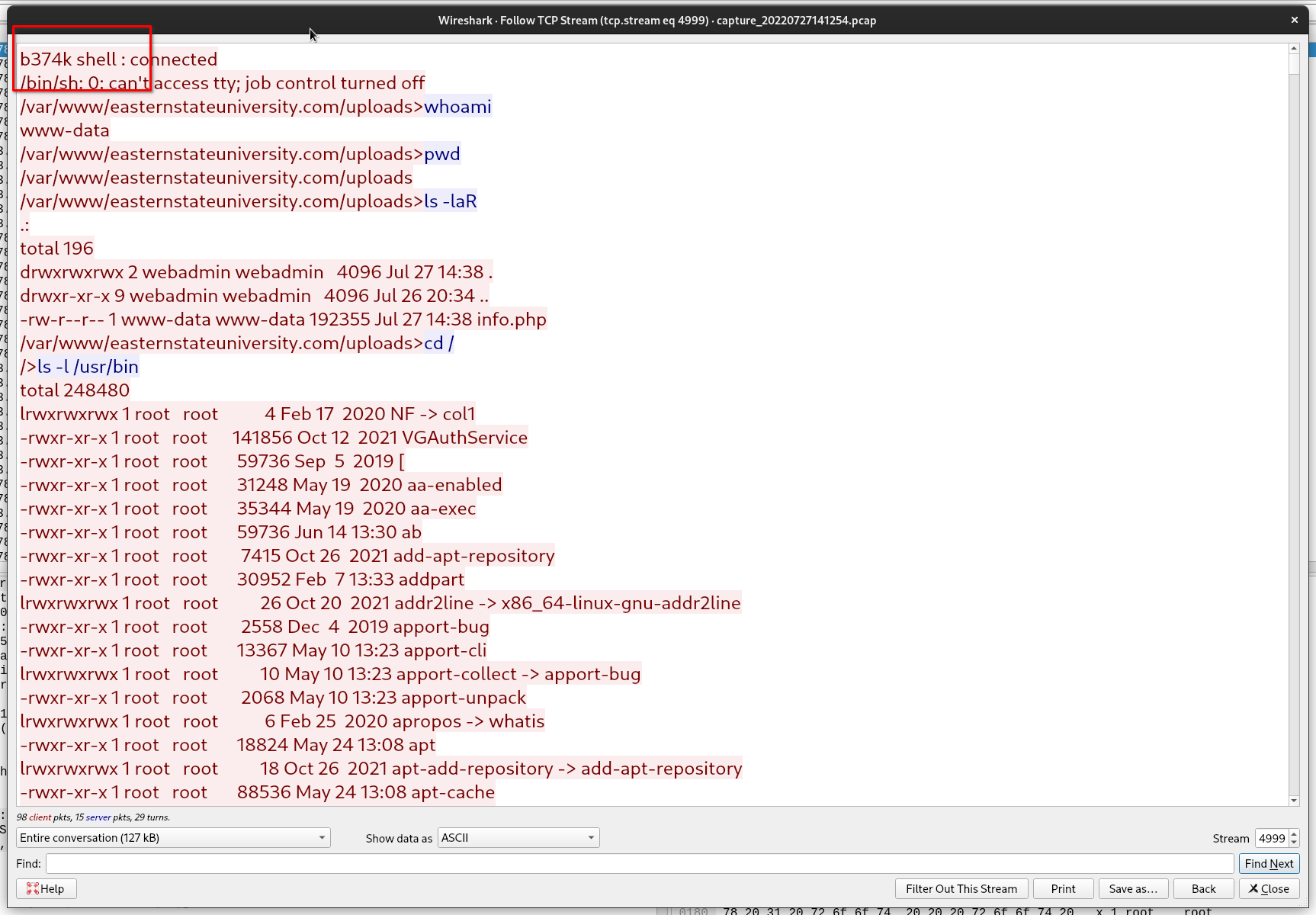
flag{b374k}