Instructions
Using the memory dump file from Window Pains, find out the name of the malicious process.
Submit the flag as flag{process-name_pid} (include the extension).
Example: flag{svchost.exe_1234}
Prerequisites
Python requirements.txt:
volatility3
yara-python
pycryptodome
capstone
Solution
Use the volatility malfind function to search for and dump memory ranges that potentially contain injected code.
Use Clamav to search for known malware.
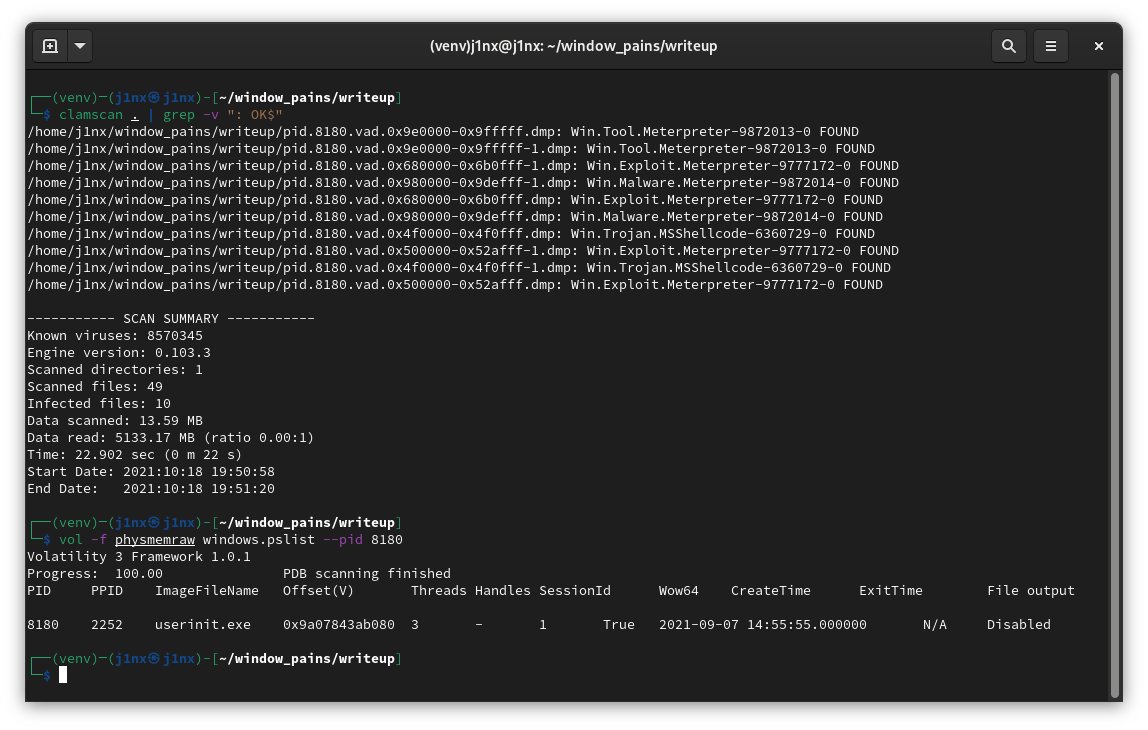
Pid 8180 appears to contain known malware signatures. Use the volatility pslist function to get more information about the process.
flag{userinit.exe_8180}